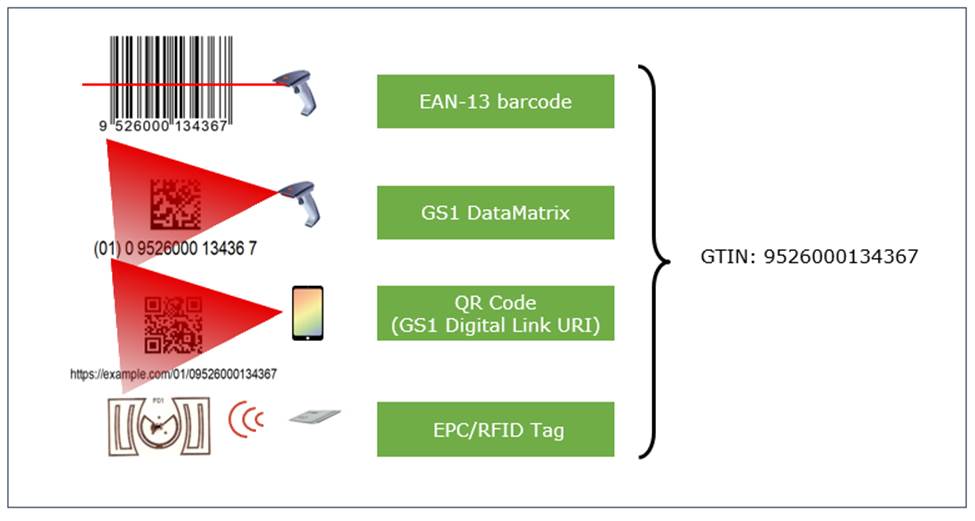
6.5 Layering of interface standards – Content vs. Syntax vs. Transport
GS1 standards that define interfaces facilitate interoperability between different system components deployed by end users. They are typically specified in three layers. All standards in the Share layer, as well as some infrastructure standards in the Capture layer, are designed in this way.